When logging in to many sites, the user is required to enter a short code from a two-factor authentication application. This is not always convenient, but it is safer. Agree, would it be cool to have a feature like this when communicating with people online?
When logging in to many sites, the user is required to enter a short code from a two-factor authentication application. This is not always convenient, but it is safer. Agree, would it be cool to have a feature like this when communicating with people online?
Why is this necessary?
Have you ever had a colleague ask you to lend money before payday, you agreed... And then in the general chat, they write that the colleague’s account was stolen, and it was not worth communicating with him?
Using the ShakeMyHand app, you can try to avoid such situations. After all, it allows you to generate two-factor codes for people.
At the time of writing, the application is only available for iPhone. An Android version is in development.
How it all works
Just like regular 2FA apps, ShakeMyHand generates unique codes and updates them at regular intervals. And their values are always synchronized between all devices.
Working with the application does not require you to have any special knowledge in the field of security or complex configuration. The entire installation process takes just a few steps.
You and your friend must both install the application on your smartphone. To create a code, you need to click the Add first handshake button and scan the resulting QR code on your second smartphone.
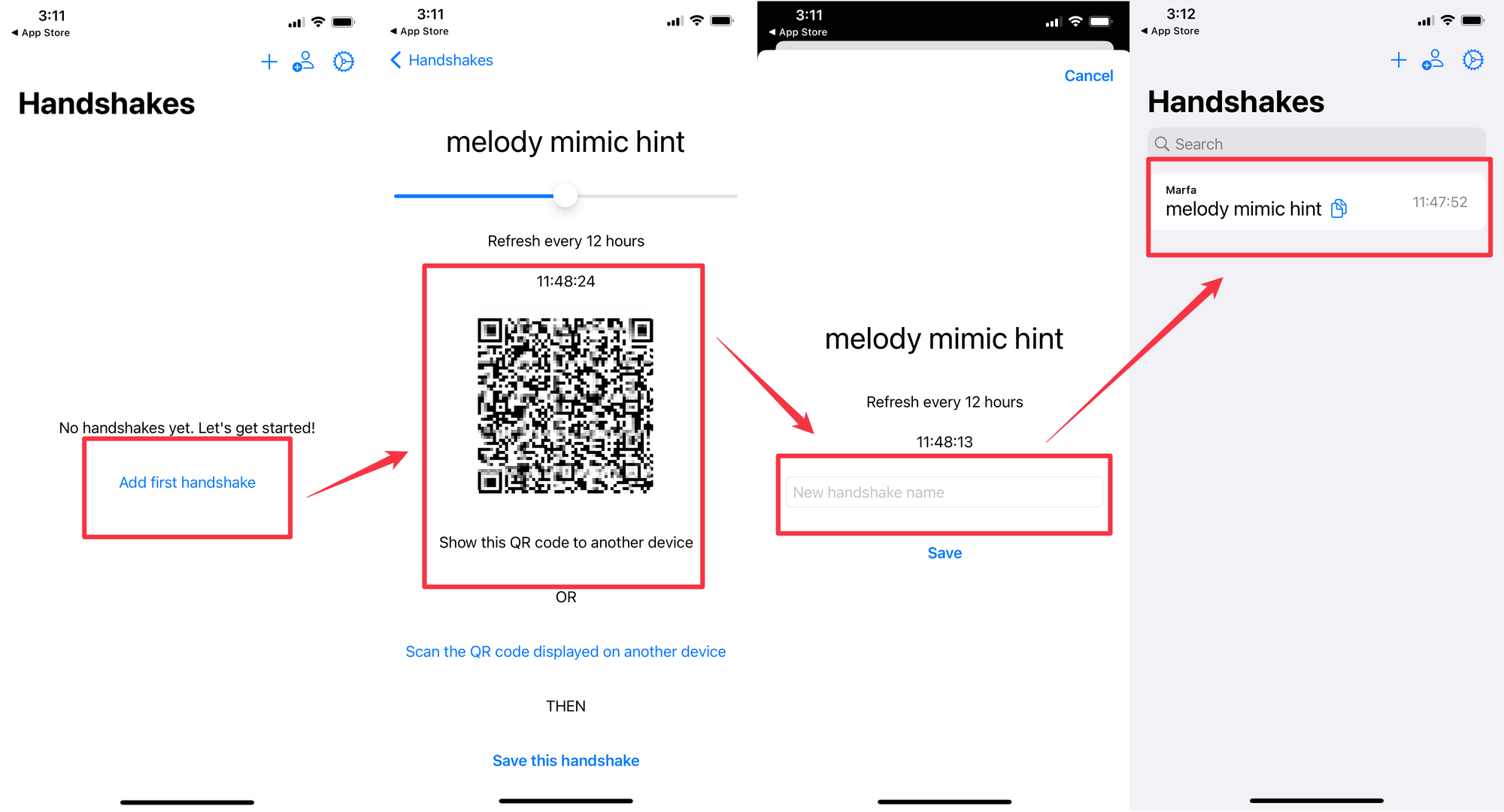
After which, you need to repeat the operation from the second smartphone so that you both have each other’s verification codes. Of course, the initial exchange of codes should be done in person, then you will be completely sure that this is the right person.
The benefit of ShakeMyHand is that it allows you to generate unique two-factor authentication codes to communicate with specific people. This is especially useful in situations where you need to verify the authenticity of your interlocutor in an online dialogue.
This eliminates the possibility of manipulation by attackers, since when communicating online, you can always easily verify the identity of your interlocutor. And the next time you suspect something is wrong, you can simply ask for the code from the application and compare it with the generated value.
