CrypTool is a modern project designed to develop open source code. Today it is extremely widespread and is used to study cryptology.
Cryptography is the science that ensures the confidentiality of information, integrity and the ability to authenticate the authenticity of authorship or other parameters. At first, its formation as a science, cryptography was mainly studied the methods of encrypting data using a secret algorithm. Today it has several forms and is used in different industries, including information technology.
This is autotranslated version of this post.
In contrast to cryptography, which provides encryption, cryptanalysis, exploring ways to decrypt information without using a key. Thus defined, the reliability and vulnerability of cryptographic algorithms and protocols. Cryptanalysis was based on the laws of linguistics, but with the development of this research area were included and various mathematical methods. The information processing is performed cryptanalytic computers, and special programs, such as CrypTool.
CrypTool: characteristics and features
CrypTool is a modern project designed to develop open source code. Today it is extremely widespread and is used to study cryptology. CrypTool detailed, explains the whole set of algorithms used in cryptography, and there are over 400 species.
Includes almost all types of classic fonts, as well as modern variations of cryptography, such as:
- Symmetrical;
- Asymmetrical, including RSA;
- The ellipticity;
- Electronic signature;
- Hybrid encryption;
- The key exchange Protocol is Diffie-Hellman.
The aim of the project is to educate users of cryptography to address network threats, ensuring the security of their data. CrypTool contains some types of didactic games and an active program to explain the basics of the theory of numbers. Today there are four variations of software that are actively developing. They are available in six languages. Each algorithm, in addition to detailed descriptions, is implemented and the user can both encrypt and decrypt a particular set of information.
Symmetric cryptography
CrypTool contains a large number of classical ciphers. The most simple and therefore popular is the Classic Cipher (Caesar). It is better known as a shift cipher, in which each text character is replaced by another situated at a certain distance to the right or to the left in the alphabet. The Caesar cipher can be used as an independent method or in combination with others, as Vigenere cipher or ROT13.
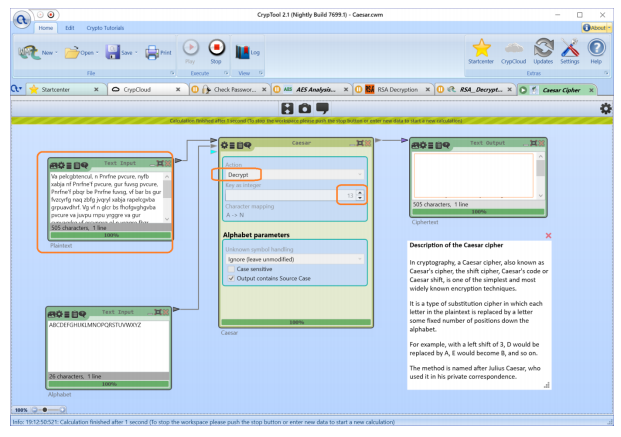
Utility CrypTool includes many versions of Modern Ciphers. AES (Advanced Encryption Standard) widely izveschenie and as Rijndael. He is the modern standard for the various symmetric block cipher and is widely used by the U.S. government, which is a striking proof of its reliability and vzlomobezopasnost. In addition, the acceleration support was introduced by Intel in the composition of the x86 processors.
The algorithm of operation of AES consists of two processes, namely:
- Algorithm expansion key (generating round key);
- Key algorithm iteration (selection round key).
Asymmetric cryptography
Asymmetric Cryptography is encryption, the public key transmitted via an open (unsecured) channel. Such systems are widely used in diverse network protocols: TLS, SSL, SSH, PGP, S/MIME.
RSA Cipher allows you to generate a few large numbers so that, having the public key, impossible to compute private. At the same time, the mechanism by which the process of generation, is well known.
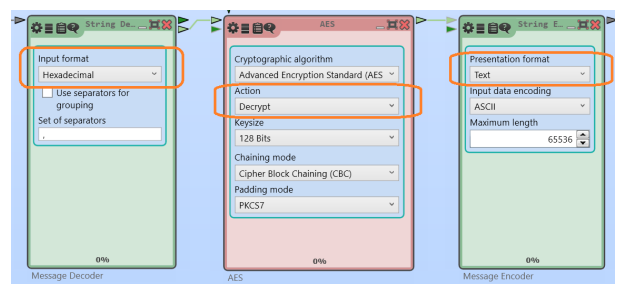
The second of the principles of asymmetric cryptography is that there are very reliable methods of encryption that encrypts any message a public key, but for decryption you must have and a private key.
Also if a person has both keys, it can transfer outdoor other stakeholders, making it well-known. Transmitting a message to the owner of the keys public key counterparties encrypt the information, and deliver it via open channels. But to decrypt the information can only be the owner, as only he has the private key. Thus, asymmetric cryptography is a reliable way of data protection. However, to prevent information leakage, the key must remain secret to everyone else.
To obtain the private key in CrypTool "template Factorization QS". Then the template is applied "RSA_Decryption" are entered the desired values. We then introduce the resulting encrypted data, and using the template to produce the decryption. Experts say that the longest constructed and laid out module had 768 bits. However, suppose that the RSA modulus can cope with 1024-bit keys.
Assay procedure secure passwords in CrypTool
CrypTool has various functions of key generation, and hash functions. They are in the list of templates in Startcenter. Modern hashed passwords use different input functions of the keys. Password strength is checked by a specialized template "Check password strength". CrypTool provides information about the security level of the analyzed password. If it is low, you can try to modify it by adding letters (including uppercase), numbers and symbols. Based on the data the utility that the password has been reliable, has a length, rather than the complexity of the combination of symbols.
Where to study cryptography?
There is a special e-learning platform cryptography — JcrypTool. It is designed for a wide range of users. It can be as teaching staff of specialized educational institutions, students, developers, and other people who are interested in cryptography, I wish to learn and use cryptographic algorithms to learn how to analyze them.
On the online platform has all the conditions not only for familiarization with specialized algorithms, and methods for their use, but also for learning to develop their own cryptographic plug-ins. This contributes to the continuous development and expansion of the JCrypTool platform in new directions.
CrypTool recognized by leading industry experts and has several prestigious awards in the field of educational programmes, namely: EISA 2004, TeleTrus Special Award 2004, security Award NRW 2004 IT and others. This confirms the utility and practicality of the software.
